
Security
Microsoft has gone to some efforts to make Vista the most secure version of the operating system yet. XP has been plagued with security problems - from the constant Internet Explorer exploits, to problems with Outlook Express, to non-internet related problems like user account privileges. Thankfully, Vista delivers, to some extent, on the promise of a safer operating environment.User accounts:
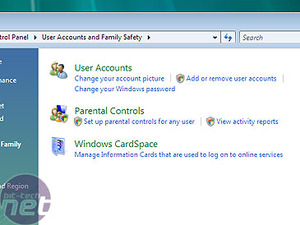
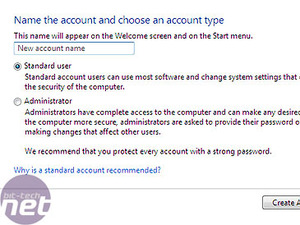
One of the biggest problems with internet malware is that, when it executes on a system, it tends to do so with the user privileges of the user currently active. Since almost everyone runs Windows XP as an Administrator, the malware has complete access to the system. Why does everyone run as admin? Because doing anything on XP requires high-level privileges.This has been addressed in Vista. It is now possible to do everything that you would want to, day to day, from a limited privilege account. Installing programmes, making desktop changes etc - none of that requires anything above the basic account. If you need to do something that requires admin-level privileges, the system will just ask you for the password, rather than making you reboot into a higher level account. This means that malware should find a slightly harsher climate within Vista.
BitLocker Encryption.
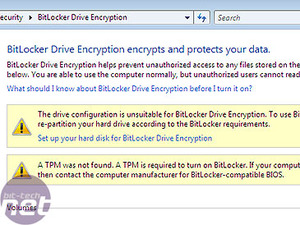
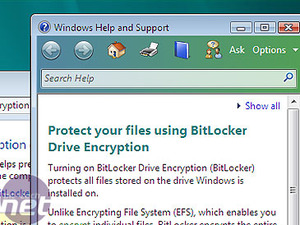
Rather than security for your system, this is security for your data. BitLocker enables you to keep a hard disk volume on your machine permanently encrypted. You can drag and drop files on and off it, and open them from within the Locker, where they are decrypted on the fly. There are a couple of ways of doing this. To generate the key, you will need a Trusted Platform Module inside your machine, which generates a machine specific key which is used to encrypt the data. Should the drive be removed from the system, it will not unlock, since it will lack the key stored on the TPM.Alternatively, you can encrypt the drive using a key generated by the software and stored on a USB key. The drive will not be readable without the USB key. This seems like a better idea, since it means that having a laptop stolen will not function. However, it does mean that, if you lose the USB key, you are stuffed.
BitLocker is a very, very welcome addition to Vista. Privacy is a growing concern amongst users, and laptop theft is a massive problem. A USB key as a decryption method is simple, yet somehow inescapably cool; James-Bond-Like. However, you'll only get it on Business and Ultimate versions of Vista.
Address Space Layout Randomisation:
This is something that is designed to prevent exploits that execute code on the host machine. Often this can be done by causing buffer overruns, and writing code to specific areas of the memory. This is fairly easy to pull off, since Windows memory mapping operates in a standard way. However, with ASLR, the memory map is randomised, so that it alters from system to system to system. This makes it much harder to write code that will guarantee that an exploit can run on a machine, since the target area for the exploit will be randomly different.Root improvements:
There are some big low-level changes in Vista that should make a difference to the overall security map. Most drivers now run at the user level of authorisation, rather than at the kernel level. There is also a new networking stack. This is a double-edged sword: whilst it is better designed than in XP, providing more functionality and fixing some old problems, new code is inherently less secure than old code, and the proof of security in the new networking functionality will only come with time.64-bit improvements:
There are a couple of further security enhancements in the 64-bit version of Vista. Why only in 64-bit? Well, these security improvements will break backwards compatibility with many hardware and software packages, which Microsoft is not keen to do, generally. If you're savvy enough to upgrade to 64-bit Vista, chances are that backwards compatibility isn't as much of an issue for you anyway since you have a newer machine, so the theory goes.Programmes are prevented from getting their claws into the Windows kernel in the 64-bit OS. This has been a common tactic for programmers in the previous version of Windows, who have patched code into the shell to obtain the kind of functionality they require. For instance, many virus scanning programmes use kernel hacks to intercept problems and rogue code before Windows gets hold of them. The downside is that malware can also hack right in, too, compromising your system. In 64-bit Vista, this kind of hacking is locked right down, and kernel patching simply cannot be done, preventing malware from executing in a stealthy kind of way. The downside is that some software will break, but them's the breaks.
Device drivers have been a major source of instability and insecurity under the WinXP regime. For 64-bit, any device must have a device driver that is signed by either Microsoft or VeriSign, authenticating it with the operating system. Anything that isn't properly signed simply won't install.

MSI MPG Velox 100R Chassis Review
October 14 2021 | 15:04








Want to comment? Please log in.