
Mob history
The last flash mob from the Artists, number 13, was last Wednesday and Thursday. Here's a quick history of the Flash Mobs so far:- 30th November 2003. The first ever 419 Flash Mob killed a single fake bank site with the Fake Banker's Nightmare.
- 2nd February 2004. At the second Flash Mob the goals were set a little bit higher and aimed at five fake banks at once. All five banks were put out of business in less than 24 hours.
- 1st March 2004. The third Flash Mob involved people from all over the world, and successfully shut down 27 fake banks.
- 1st April 2004. On World's Fools Day, the fourth Flash Mob shut down 19 fraudulent sites in less than 24 hours again.
- 3rd May 2004. Another 17 fraudulent sites were shut down completely and life made difficult for 25 others during the fifth Flash Mob
- 1st June 2004. The sixth Flash Mob had great success: the first bank shut down within 15 minutes and others fell throughout the day.
- 1st July 2004. During the seventh Flash Mob, flash mobbers nuked 6 fraudulent sites!
- 1st August 2004. Five fake lotteries went out of business during the eighth 419 Flash Mob.
- 1st October 2004. On Nigeria Day 2004 they nuked 3 fake banks for the ninth Flash Mob!
- 1st November 2004. For the tenth Flash Mob, the Artists spooked scammers when the Halloween Flash Mob killed 6 fake sites!
- 9th February 2005. To celebrate Chinese New Year 2005, the Artists held a special Chinese New Year Flash Mob and took out 8 fakes on Chinese servers, as well as a bunch of others on the side!
- 8th August 2005. In Flash Mob number twelve, they killed fifteen fakers (three more than expected) in forty-eight hours!
The Halloween '05 Mob - 2-3 November 2005
The results of the last mob can be found right here! In summary:- 9 sites were taken down during the mob
- A further two were left limping along
- A whole bunch of letters were sent to ISP complaint departments
- Internic got a load of domain name abuse complains
The technology
The guys at the AA419 use a couple of tools to do their Slashdot-esque antics. The first is called 'The Lad Vampire'. This is a really simple, web-based tool. It loads images from websites which are known to be sites belonging to fake banks, and then constantly refreshes them. The constant refreshing takes up a large chunk of the site's bandwidth, especially if there are hundreds of people all running the tool at the same time. However, even though it's refreshing the images at the scammer's end, it doesn't do it at your end, meaning that you don't kill your bandwidth in an altruistic folly.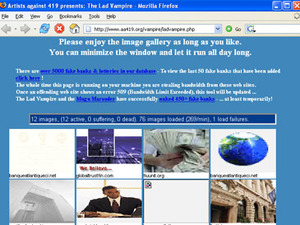
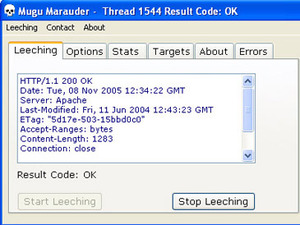
The second tool is called the 'Mugu Marauder'. This does a similar thing, but is a Win32 client. In the same manner as a distributed computing client, the Marauder records the amount of bandwidth you consume and then can rank you amongst the Artists.
The homepage of the Artists also hotlinks images from scam-banks, meaning you're doing something to help just by loading the page!
The legality of DIY anti-scam
The ethics and motives of the Artists are certainly to be commended. They work closely with ISPs that will support them, but one can't escape the nagging question - is this right, and is it legal?Some would argue that the bandwidth attacks perpetrated by the Artists constitute hacking. In the UK, hacking is regulated by the Computer Misuse Act 1990. The Act was passed to prevent damage done by hacking, and makes a couple of different provisions.
The first is simply unauthorised access to data. This can include guessing or hacking passwords to get into data not belonging to you. The second is the same unauthorised access, but with intent to commit a further criminal act such as fraud or theft.
The use of the Lad Vampire, under these rules, would appear to be a grey area. The Act specifies 'unauthorised access'. The use of the tool simply makes multiple HTTP requests, and since HTTP is the method by which the web pages of bank scammers would be viewed anyway, there's arguably no unauthorised access, since HTTP requests are explicity authorised.
However, there is an argument that whilst the 'method' of access is authorised, the 'mode' of use is nonetheless unauthorised. The images are being taken out of context, and the access could be said to be unauthorised based on the fact that the images aren't being accessed in the manner intended or envisaged. The difficulty is that once something is put out on the web, regulating its use is difficult, and there's currently no restriction on how legitimate access is manipulated. The other difficulty is that 'unauthorised' is a very vague term with no strict definition.
Taking down the website is a classic Denial of Service attack, but the Artists are very clear about stopping the attack before that occurs. They're not taking down the website - they're just pushing the limits of the cheap-and-cheerful hosting the scammers have used. This would appear to keep them short of causing legal damage.
At the very least, the constant displaying of the images would possibly constitute copyright infringement, since laws regulate what you can do with images that are other people's property and appear on other people's websites. Of course, the bank scammers don't actually own the copyright in the images, we suspect, so that argument won't fly.
The practicalities are that since the Artists are so careful not to hurt non-scammers, the likelihood of anyone actually complaining to the Police about them is minimal. Without a complaint, the Police aren't likely to start investigating the Artists of their own accord and even if they did, it would take a full trial in a court to establish the legality of their actions. The realities of the British criminal justice system are that this is unlikely to happen any time soon, unless the Artists get something wrong and overstep the mark.
bit-tech cannot condone people taking the law into their own hands and participate in Flash Mobbing, even if the net result makes the Internet a safer place to live. It is arguably White Hat and the letter-writing and liaising with ISPs is a smart and safe approach to the problem. Bringing sites down is technically more Black Hat, though considering the target, it could be classified as Grey Hat.
We encourage all readers to start by educating less knowledgeable users - family, friends, co-workers - about the dangers of 419, and other phishing activities. These criminals rely on a certain number of guillible people falling into their trap, so let's starve them of victims.

MSI MPG Velox 100R Chassis Review
October 14 2021 | 15:04








Want to comment? Please log in.